Right at the moment a Safari user visits a website, even if they’ve never been there before or entered any personal information, a malicious website can uncover their first name, last name, work place, city, state, and email address. Safari v4 & v5, with a combined market browser share of 4% (~83 million users), has a feature (Preferences > AutoFill > AutoFill web forms) enabled by default. Essentially we are hacking auto-complete functionality.
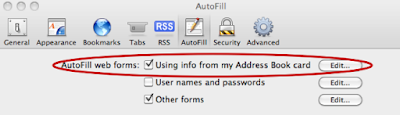
This feature AutoFill’s HTML form text fields that have specific attribute names such as name, company, city, state, country, email, etc.
 <* form>
<* form><* input type="text" name="name">
<* input type="text" name="company">
<* input type="text" name="city">
<* input type="text" name="state">
<* input type="text" name="country">
<* input type="text" name="email">
<* /form>
These fields are AutoFill’ed using data from the users personal record in the local operating system address book. Again it is important to emphasize this feature works even though a user never entered this data on any website. Also this behavior should not be confused with normal auto-complete data a Web browser may remember after its typed into a form.
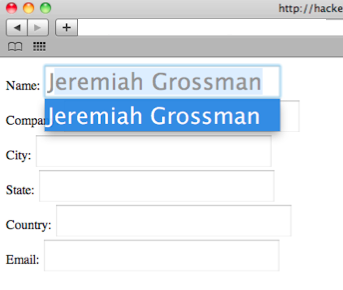 All a malicious website would have to do to surreptitiously extract Address Book card data from Safari is dynamically create form text fields with the aforementioned names, probably invisibly, and then simulate A-Z keystroke events using JavaScript. When data is populated, that is AutoFill’ed, it can be accessed and sent to the attacker.
All a malicious website would have to do to surreptitiously extract Address Book card data from Safari is dynamically create form text fields with the aforementioned names, probably invisibly, and then simulate A-Z keystroke events using JavaScript. When data is populated, that is AutoFill’ed, it can be accessed and sent to the attacker. As shown in the proof-of-concept code (graciously hosted by Robert "RSnake" Hansen), the entire process takes mere seconds and represents a major breach in online privacy. This attack could be further leveraged in multistage attacks including email spam, (spear) phishing, stalking, and even blackmail if a user is de-anonymized while visiting objectionable online material.
Fortunately any AutoFill data starting with a number, such as phone numbers or street addresses, could not be obtained because for some reason the data would not populate in the text field. Still, such attacks could be easily and cheaply distributed on a mass scale using an advertising network where likely no one would ever notice because it’s not exploit code designed to deliver rootkit payload. In fact, there is no guarantee this has not already taken place. What is safe to say is that this vulnerability is so brain dead simple that I assumed someone else must have publicly reported it already, but exhaustive searches and asking several colleagues turned up nothing.
I figured Apple might appreciate a vulnerability disclosure prior to public discussion, which I did on June 17, 2010 complete with technical detail. A gleeful auto-response came shortly after, to which I replied asking if Apple was already aware of the issue. I received no response after that, human or robot. I have no idea when or if Apple plans to fix the issue, or even if they are aware, but thankfully Safari users only need to disable AutoFill web forms to protect themselves.
Video Demo
Fortunately any AutoFill data starting with a number, such as phone numbers or street addresses, could not be obtained because for some reason the data would not populate in the text field. Still, such attacks could be easily and cheaply distributed on a mass scale using an advertising network where likely no one would ever notice because it’s not exploit code designed to deliver rootkit payload. In fact, there is no guarantee this has not already taken place. What is safe to say is that this vulnerability is so brain dead simple that I assumed someone else must have publicly reported it already, but exhaustive searches and asking several colleagues turned up nothing.
I figured Apple might appreciate a vulnerability disclosure prior to public discussion, which I did on June 17, 2010 complete with technical detail. A gleeful auto-response came shortly after, to which I replied asking if Apple was already aware of the issue. I received no response after that, human or robot. I have no idea when or if Apple plans to fix the issue, or even if they are aware, but thankfully Safari users only need to disable AutoFill web forms to protect themselves.
Video Demo
72 comments:
This can seemingly affect Chrome/Chromium too. In that it's not so clear how to delete things from autofill...
What makes you think that? I use chrome and I saw some of my information pop up as it went through the letters, but the website didn't appear to receive that information (nothing appeared after the colons). I think chrome's auto-fill relies on popups that don't actually input your info into the form until you hit enter. Whereas Safari just directly inputs your info into the form.
Tom:
Ah good point - I did not see anything after the colons - I only saw the suggestions flashing by and assumed they had been submitted.
Awww, good thing I haven't been using Safari for a while (now exclusively a Firefox guy). Good info, Jeremiah.
This is very good to know!
Originally saw this discussed at http://weblog.patrice.ch/2009/04/09/safari-autofill-birthday.html back in April 2009
Sorry for slight OT, but "<* input>" with unescaped "<" hurts my eyes. Doesn't Blogger allow proper HTML entities?
@Anonymous, Tom: I believe this may be a WebKit issue and not just Safari. While it is difficult to confirm now, I suspect this technique did in fact affect Chrome. Had some discussions with Google a while back surrounding this topic and recall them finding/fixing something, but I don't really get all the details straight. Will have to find an older Chrome version somewhere to confirm...
@Harryf: good find, that is vaguely similar and potentially offers a way to make this more efficient.
@klkl: it does, sorta, but getting it to work is more difficult than it should be. At least for me. :)
Note that this does not appear to work under Windows or iOS, as, although the option is ticked by default, Safari doesn't actually *know* your details, so it couldn't leak them if it tried.
Easy enough to disable in Safari>preferences>autofill. Just uncheck the options.
Very good implementation. I love it! By the way, I think you already knew about it based on:
http://ha.ckers.org/blog/20060821/stealing-user-information-via-automatic-form-filling/
Are these issues the same things?
@Soroush: related, but not identical. that post / technique was leveraged using XSS... this technique uses keyboard event simulation and gets very browser specific. Often enough this sort of research takes years to fine tune and get straight.
JG, great tweet! This type of infringement as well as WiFi spying, i.e. data capture over unsecure networks, is on the rise. We at SwissDisk give free secure, end-to-end encrytped accounts to anyone who wants to keep their private info private. Watch your settings people! Stay safe out there in the wild wireless world aka the www.
Maybe I'm not thinking this through, but you can get a lot of information through publicly-available information about your IP address. MaxMind and other geolocation services have pretty granular information about where IPs are located. Not to mention that ARIN makes available who owns a particular IP, and if you're surfing from work, the owner of the IP you're on will very likely be your employer. And, most sites log the IPs of their visitors. So, it seems bad to leak info from your address book, but just because you don't doesn't mean the sites don't know where you are or potentially where you work.
I'm on Safari 5, the example "exploit" code you linked went through A - Z for each field and didn't get any info. All fields blank. I have Autofill on, I have a "Me" card in my Address Book. I can Autofill my info when I'm on a website. So what gives? Maybe I'm misreading your post, but I'm not seeing any "exploit" here.
How did you report this issue to Apple?
Chrome requires a user gesture for auto fill so firing key events shouldn't work. If it does please report it.
Does it work with iPad or iPhone?
I had exactly the same result as Anonymous up there -- on Safari 5, autofill on, "me" card selected, works on sites I frequent, zilch on the proof of concept. This may work on v4, but it looks to me like v5 already has this patched.
It works on Safari Version 5.0 (5533.16), Mac OS X Version 10.5.8.
@anonymous: I informed apple through the product-security@apple.com email address they recommend. I know it got through because it sent me an auto-response.
@anonymous: this hack may have worked on Chrome at one time, but no longer. Trying to confirm, but difficult to get old OS X copies. :)
Interesting that people are getting mixed results on it working or not. I did confirm with several people on several systems ahead of time.
@ Jeremiah Grossman: Does it work with iPad, iPhone or iPod browser?
@naccio: no, it does not. Mobile Safari's behavior is different. Im sure mobile browsers have their own issues, but I haven't spent quality time on them with security testing yet.
Thanks God I am using IE 8!
IE8 FTW!!! lol !!!
security wise anyway, could do with a rocket up its arse mind!
All of my Autofill information from the address book is fake anyway. Big deal.
Just select, in Address Book, as your personal card, a fake card, the fake card entries will be returned in the POC.
Did nothing for me on safari5
Safari 5.0 (6533.16) on Mac OS X 10.6.4 here.
The proof of concept page revealed all of my personal information. I disabled autofill and it didn't find it. Thanks for the heads up on this one.
Does the website have to know the user's name? If they auto-populate the wrong name, why would AutoFill fill in my information?
How to clear the autofill that is remembered by the webbrowser?
Also works for me on 10.6.4, Safari 5 (Build 6533.16).
I seem to recall that Autofill was disabled by default in Safari. Is that still the case?
Regardless, I've disabled that particular preference.
Is there a selective script blocker out for Safari yet? I'd prefer a whitelist, since I don't find JavaScript to be much of a necessity for the majority of sites I visit (much like Flash). However, it would be nice to enable it for a few trusted sites.
Thank you very much for the heads-up.
It works with my Safari Version 5.0 (6533.16), even *when* "private browsing" is enabled.
If Apple doesn't want to acknowlege this issue, that's quite alright. Because it's now the top item in Googles "How to of the Day." Hence, about 1/2 billion people worldwide know about it now. Good job, Jeremiah!
@Anonymous: no, the website doesn't need to know your username for this to work.
@Blog Tactic: Preferences > AutoFill > Other Forms > Edit. Clear them all that way.
@Anonymous: this feature is enabled by default. And Im not sure if NoScript or an equivalent is available for Safari yet. Probably because the available APIs necessary to not exist.
@MM: Your welcome, thanks for the comment. And there is no such thing as "private browsing." :)
@formeat: Amazing, thanks for pointer!
Unfortunately too many companies care little about privacy - Take amazon.co.uk, it uses information to display what you previously browsed on their web site even when you haven't logged on. Any user ofthe computer can see your browse history.
They seem to think this is a good feature!
Great post, did you report this issue to Apple?
This only works if you've entered that data into the address book, and then the site owners would have to extract it using javascript, so if you run things like noscript (or just javascript disabled), this is a non-issue.
When I opened my Preferences to disable the address book autofill, I noticed that the username and passwords was also enabled. I have now disabled it, but how serious an issue would that be?
I know next to nothing in Javascript and HTML form, and I wonder if it is really possible that this information gets sent to the server without the user's pushing a button to submit the form.
Otherwise, it means for instance that a website could have access to what I type in a field, even if I later change my mind and change th content or choose not to submit it.
Also, I downloaded the web page and changed the input field type to "hidden". When I click "Start", "Searching "name": appears, but that's all I see. I never goes to the next fields.
So, is it really possible to exploit this invisibly as you mention in your article ?
This combined with the a:visited problem can be really serious.
@ps, " I wonder if it is really possible that this information gets sent to the server without the user's pushing a button to submit the form"
Very definitely possible. The javascript will "push" the button for you. (Using ajax/xhr etc, this info can get sent without you seeing the page change)
@book publishers: Yes I did, over a month ago. Two emails, but not a word of confirmation or action ever came of it.
@Anonymous: Is NoScript available for Safari? And most OS X users have a "me" card as a result of the registration process.
@Anonymous: Ideally all auto-complete preferences should be disabled. The data contained within is hard, but not impossible to collect.
@PS: this data can absolutely be stolen and transferred back to the website. I didn't put in that code on purpose, but it is indeed really easy. On the invisibility, the only reason it is visible is for demonstration purposes. A little bit of CSS opacity does the trick.
Thanks for your replies. To me, this looks more like a problem with JS being able to things it shouldn't be allowed to do, such as sending the data without user interaction.
Autofill by itself is a great tool for me. Almost every day, I find myself requesting product information from companies who requires me to fill in a form beforehand. Having the form fill itself automatically is a real time saver.
Thanks for the heads up, Mr. Grossman.
This exploit does work on my system (10.6.4). Safari Version 5.0 (6533.16). Watched it go through the letters and nab my info. Will be disabling autofill.
Simply set input style to "margin-left: -500px", include MooTools (http://ajax.googleapis.com/ajax/libs/mootools/1.2.4/mootools-yui-compressed.js) and put following code before the body closing tag (in script tags):window.addEvent('domready', function(){$('mine').addEvent('submit', start());}); to make the script autostart. With this snippet, you can't even realize, that your data has been sent.
Great work Jeremiah. I hope with this Apple do something about it. Apples seems to respond to the polemic (Antennagate) instead to the good intentions.
Regards.
Jonathan.
So does this affect the current version of Chrome (5.0.375.99) or not? I'm very confused
@Anonymous: Thank you.
@Marco: Yep, pretty easy to make this invisible and steal the data passively.
@Frixhias: Thank you very much. I've gotten word from Apple security that they are doing something. Don't know what or when though.
@Anonymous: No, the latest version of Chrome is NOT affected.
Fortunately any AutoFill data starting with a number, such as phone numbers or street addresses, could not be obtained because for some reason the data would not populate in the text field.
What if the script not only sent A-Z but also 1-9 (and "(")? Would that flush out Phone Numbers and Addresses? Since it is triggering on the first character of the field, the failure to send a number would seem to me to explain the "safety" of these fields.
@anonymous: I tried entering numbers into the keyboard simulation, but for some reason any string data beginning with a number wouldn't populate in the form field. So I just took the numbers out of the loop for speed purposes. But don't worry, there is another technique that is much faster to pull all the data out -- numbers included. :)
The Turbo talk at Blackhat should be fun "Jeremiah Grossman:Breaking Browsers: Hacking Auto-Complete"
http://blackhat.com/html/bh-us-10/bh-us-10-schedule.html
interesting, looks like it is caused by webkit for desktop
Is this just OS X related or does it affect windows versions too?
@Tom: thanks for the plug. going to attempt to break the blackhat record for number of attendees at a turbo talk. :)
@Anonymous: both windows and os x are affected.
Checked the exploit under MacOS X 10.5.8 Dutch :
Safari 5.0 Dutch : fetches my name, city, country and e-mail
Chrome 5.0 Dutch : my name and e-mail appear briefly but are not autofilled or fetched
Opera 10.60 Dutch : exploit doesn't work
ps : Thanx 4 the warning!
I think it's not a high critical issue, however it's good for everyone to know issues like that,
Actually malware authors looking for such alike delicate problems to do something malicious, btw, it's cool .
IOW...the security hole lies within autofill NOT javascript. hint: don't use autofill.
I tried again with Safari Version 5.0.1 (5533.17.8) and apparently they solved the problem.
It seems that Apple fixed this bug in Safari 5.0.1.
@Naccio @Anonymous: correct, it looks like the patched solved the immediate problem. Over the next couple days / weeks, I'll try some tests to see how comprehensive it really is.
Yes, fixed in Safari 5.0.1 with credit to Jeremy, see:
http://support.apple.com/kb/HT4276
(CVE-ID: CVE-2010-1796)
In the current beta of Chrome, 6.0.472.33, there are new autofill options (see http://googlechromereleases.blogspot.com/search/label/Beta%20updates). Is this affected?
Safari 5.0.2 under SL here, did not extract any of my info, "Using info from my Address Book card" was checked in prefs.
@anonymous this particular issue is now patched. but see here for the newer version:
http://jeremiahgrossman.blogspot.com/2010/09/safari-autofill-hack-lives.html
I've been using google chrome for a while but then i had to recover my pc and when i downloaded it again when i search in the toolbar where u put in websites it takes me to yahoo instead of google. how can i change that so when i write something it takes me automatically to google??
This can seemingly affect Chrome/Chromium too. In that it's not so clear how to delete things from autofill... efox-shop
Glad to find that there is a patch, but this still doesn't make me feel any better about the folks working on Safari.
SAFARI HAD BEEN SAYING AND LISTING WEBSITES THAT THEY SAY I VISITED OR ARE MY FAVORITES. I DID NOT VISIT MORE THAN HALF OF THESE WEBSITES. CAN SOMEONE TELL ME WHAT IS HAPPENING HERE??
SAFARI IS SAYING THAT I BROWSE WEBSITES THAT I DID NOT AND THAT THEY ARE MY FAVORITES. CAN SOMEONE TELL ME WHAT'S GOING ON HERE??
Post a Comment