The first graphic is my take on the “vulnerability stack”, the areas of focus for vulnerability scanning/assessment solutions. This is helpful for asking vendors what area they cover. There are probably some areas I missed, but it’s a first draft. If my technical vulnerabilities and business logic flaws terminology is confusing, please see Technology Alone cannot Defeat Web Application Attacks: Understanding Technical vs. Logical Vulnerabilities
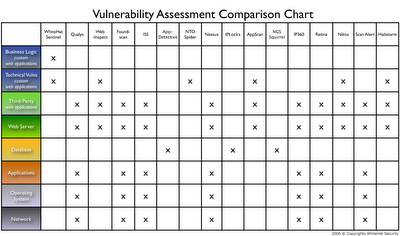
The second graphic is a vulnerability scanning/assessment vendor comparison chart. Here we’re trying to answer the “who covers what question?” and a foundation to ask how they are different. I know some will vendors claim they do more that what the chart indicates, but I’m listing only their main areas of focus. If someone happens to add a web application vuln check or two, it doesn’t make them a network scanner. Likewise if web application scanners adds a few network checks, it hardly a new Nessus. A decent amount of comprehensiveness in the block is required. Enjoy!

6 comments:
Nice chart. You might want to consider turning off the spell checker and re-exporting it...
(Not trying to be snarky, consider this a bug report and a genuine compliment in one.)
darn, that was the second time someone mentioned that, so it had to be fixed. The red underlines have been removed from the image. Thanks for the feedback!
Nice framework! Don't forget databases (ex. Oracle), packaged apps (ex. PeopleSoft), and custom apps.
Where's Internet Security Systems? A big market leader should show up, right?
Thank you for the comment and made some updates to the vulnerability stack image and added ISS to my vulnerability comparison chart. I'll probably need to update this again to match the stack image better. These should do for now though.
Security is the degree of protection against danger, damage, loss, and criminal activity. Security has to be compared to related concepts: safety, continuity, reliability. The key difference between security and reliability is that Security System must take into account the actions of people attempting to cause destruction.
Post a Comment